Signing
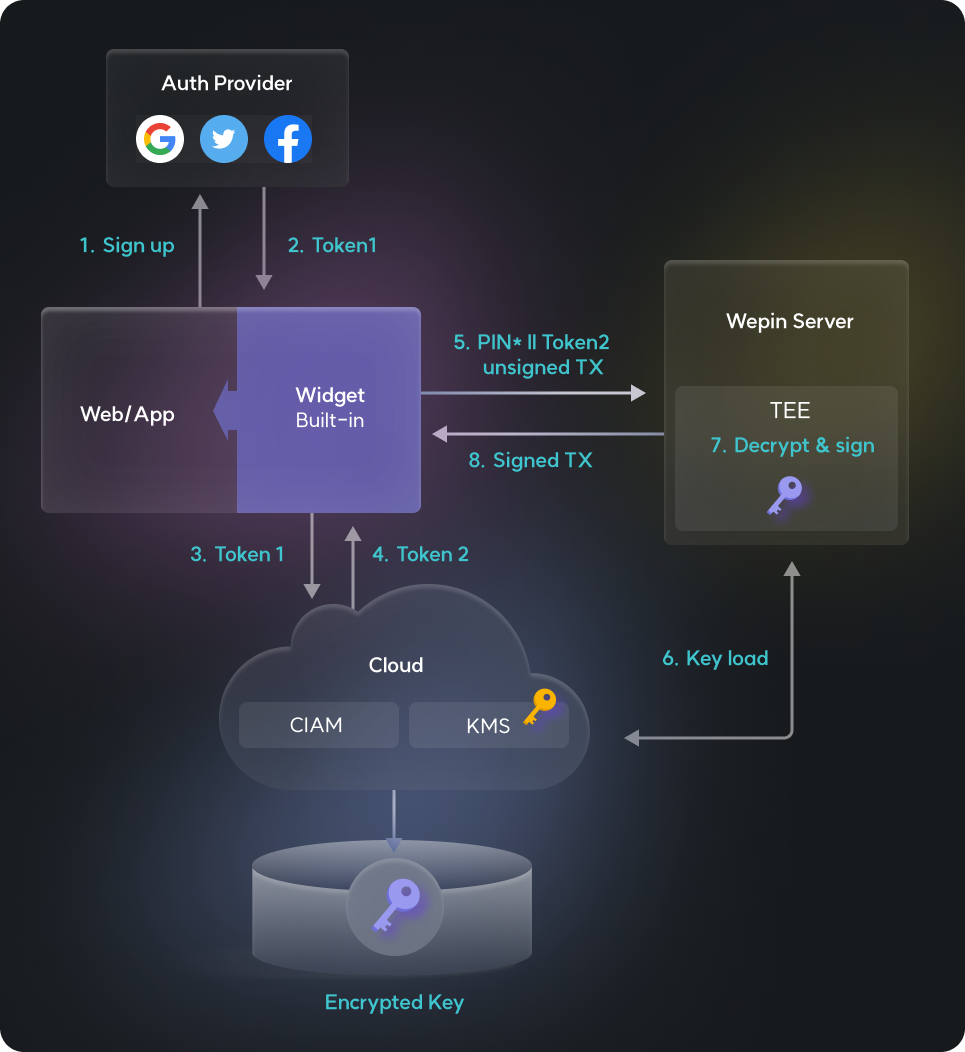
Just like the key generation procedure, logged-in users receive a token that grants access to the storage where the encrypted key is stored, and they request the Wepin server along with the transaction that requires signing. The server uses the user's token to retrieve the encrypted private key and then decrypts it using the PIN number submitted by the user. After signing the transaction with the decrypted key, the private key is securely encrypted again and stored in the cloud.
The operations for signing are also executed exclusively within a Trusted Execution Environment (TEE). Therefore, the private key loaded into memory during the creation of the signature is inaccessible to the Wepin server, meaning the server cannot know the private key information. The server merely performs the role of executing operations; the private key information remains undisclosed, and interactions throughout the entire protocol of signing a transaction occur in an encrypted form.
Last updated
Was this helpful?